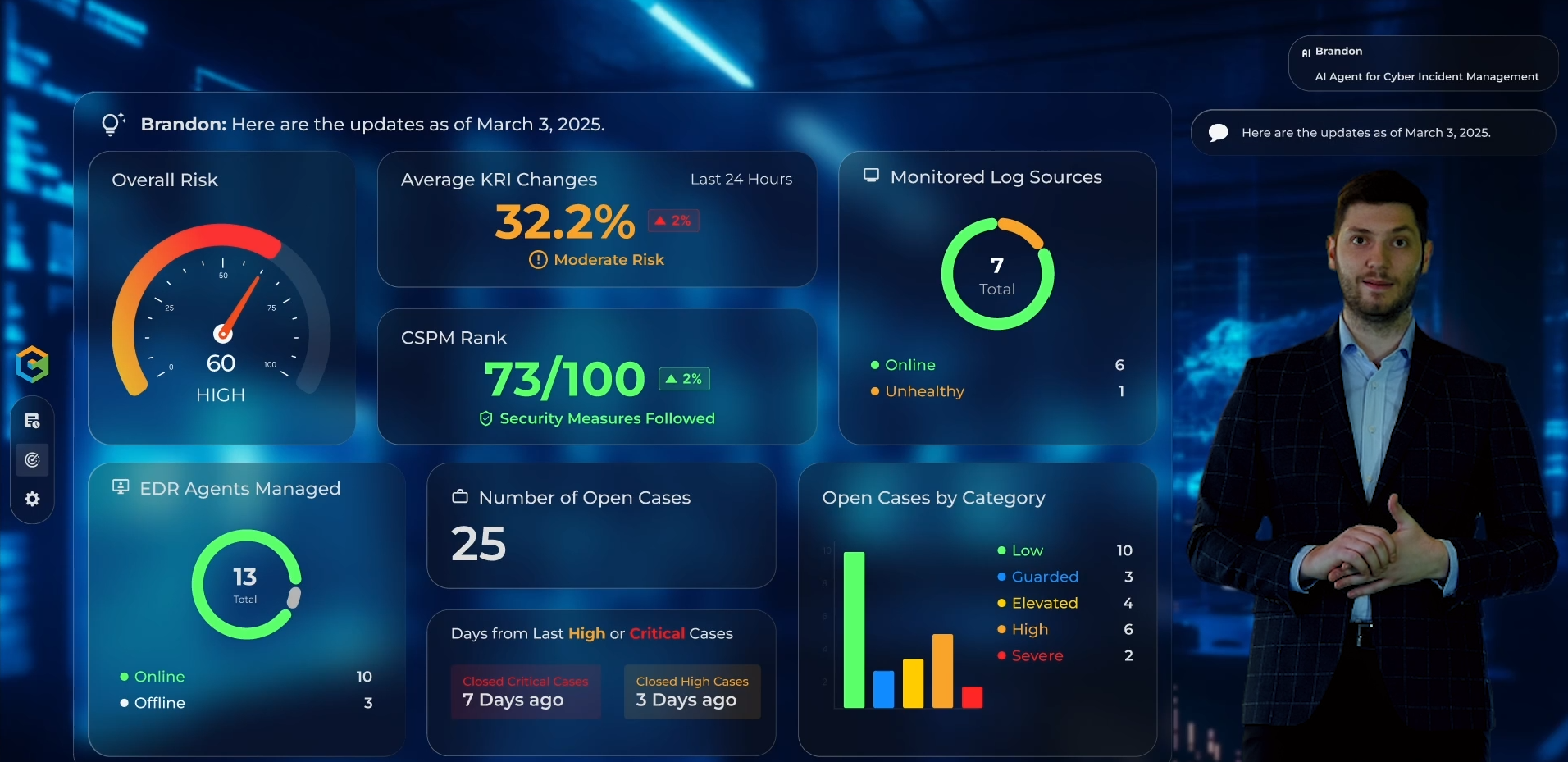
AQUILA transforms how businesses allocate cybersecurity resources by optimizing investments in consultancy and labor. Rather than broadly spending on external services or relying on generalized expertise, AQUILA ensures that your investments are precisely targeted toward those experts who deliver significant, high-value contributions to your organization.
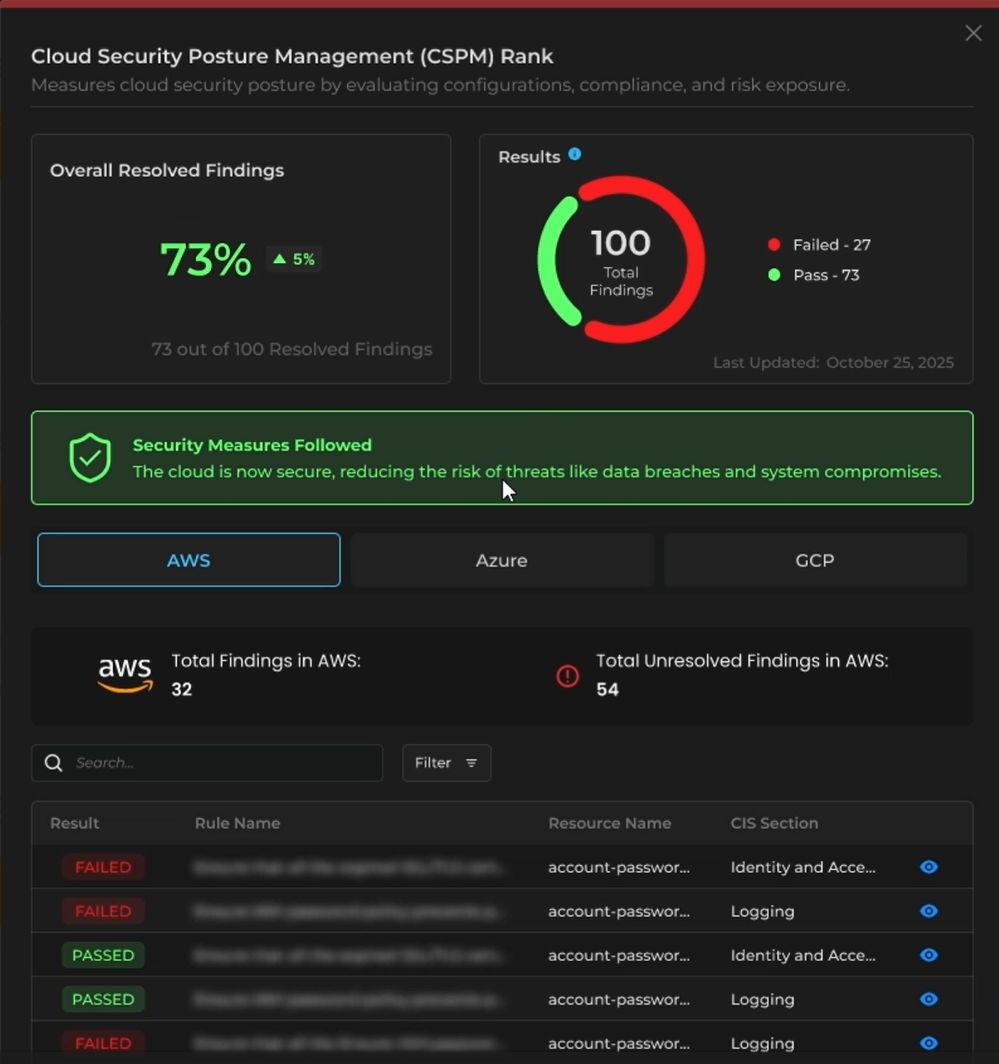
AQUILA takes cloud security to the next level with its embedded Cloud Security Posture Management (CSPM).
By integrating with leading cloud environments—Microsoft Azure, AWS, and Google Cloud—businesses can connect one or all as needed.
AQUILA continuously scans for misconfigurations every 24 hours, ensuring compliance with the most advanced cloud security standards.
This proactive approach helps businesses maintain a secure and resilient cloud infrastructure without unnecessary complexity.
